Download our free Monitoring Fundamentals Tutorial.
An introduction to Monitoring Fundamentals strictly from the perspective of telecom network alarm management.
1-800-693-0351
Have a specific question? Ask our team of expert engineers and get a specific answer!
Sign up for the next DPS Factory Training!

Whether you're new to our equipment or you've used it for years, DPS factory training is the best way to get more from your monitoring.
Reserve Your Seat TodayBeing able to effectively communicate with your workforce is of major importance in any industry. Without the ability to communicate with your team, you'll limit the amount of work you get done - and likely create serious safety risks.
Many businesses and public-safety service organizations have adopted the use of radios for instant communications. This includes police departments, fire departments, ambulance companies, and more. Trunked radio systems are particularly beneficial for these larger organizations, providing them with expansive coverage and the ability to manage multiple talk groups efficiently.
These systems not only enhance internal communication but also offer the scalability needed for organizations that rely heavily on coordinated efforts, such as logistics companies or large event management teams. By leveraging the advantages of trunked radio systems, these entities can maintain seamless, secure, and efficient communication.
There are two main styles of radios designed for this purpose: the conventional system of two-way radios and trunking radios. Both conventional and trunked systems are very similar in terms of how they work, but only one can help improve the security and efficiency of communications during use.
Standard two-way radios do not have a central server/controller. The radios simply talk directly to each other, often with the help of repeater stations. With standard two-way units, anyone can switch over to a channel and participate in your conversation - whether you want them to or not.
Unlike conventional radio systems, a variety of trunking systems allow for voice encryption and the ability to lock out radios from talk groups and even entire networks. This ensures an additional layer of security and control over communication channels. In short, trunked radio systems allow multiple groups of users to share a small set of radio frequencies without accidentally hearing or talking over each other's conversations.
Moreover, trunked radio systems enhance privacy by assigning groups to specific frequencies. This strategic allocation ensures that active groups can conduct their conversations without the worry of being overheard or interrupted by other talk groups. By segregating frequencies, these systems create a more secure environment for private communications.
A trunked radio system is a complex type of system that involves two-way radio, allowing the sharing of a few trunked radio frequency bands between a large number of users. Instead of assigning a radio channel to one particular organization at a time, users are instead assigned to a "talk group".
When any person in that group wishes to talk with another member in their talk group, the system automatically selects a channel that is vacant and the conversation takes place on that dedicated channel. Once a channel is no longer in use, it returns to the available pool to be assigned to other users.
This form of communication is a packet-switching computer network. Radios send data packets (voice messages) to a computer-controlled channel to request communications with a specific talk-group.
The controller then sends a signal to all radios linked to that talk group instructing them to automatically switch to the dedicated frequency indicated by the transmission. After the user is done speaking, all radios immediately return to the Control Channel to await further transmissions.
Through the use of trunking, radios can utilize the same sets of frequencies with less cross-talk, interruption, and errors. All messages must pass through a central computer for sorting and delivery. This method also allows for a greater volume of communications to pass through the same frequency bands. This is because as soon as a line clears, the system automatically begins to transmit the next message regardless of which talk group is active.
Since its release in 1997, and with advancements made to this technology, trunked-system users are now able to do far more in terms of securing their communications from misuse. Unlike conventional radio systems, trunking systems allow for voice encryption and the ability to lock out radios from talk groups and even entire networks.
This ensures an additional layer of security and control over communication channels. In short, trunked radio systems allow multiple groups of users to share a small set of radio frequencies without accidentally hearing or talking over each other's conversations.
Moreover, trunked radio systems enhance privacy by assigning groups to specific frequencies. This strategic allocation ensures that active groups can conduct their conversations without the worry of being overheard or interrupted by other talk groups. By segregating frequencies, these systems create a more secure environment for private communications, making them ideal for organizations that require confidential and reliable communication solutions.
In short, trunked radio systems allow multiple groups of users to share a small set of radio frequencies without accidentally hearing or talking over each other's conversations. Trunked radio systems primarily conserve limited radio frequencies and also provide other advanced security features to the users.
Other Helpful Links
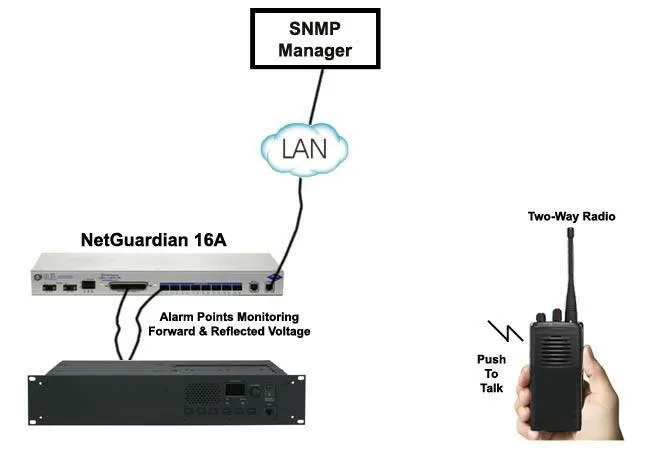
New Application: Monitor Trunked Radio Systems Frequencies for More Reliable Radio Communications
Advantages and disadvantages of Trunking Systems
Triangle Communications Boosts Network Reliability with In-House Monitoring