Check out our White Paper Series!
A complete library of helpful advice and survival guides for every aspect of system monitoring and control.
1-800-693-0351
Have a specific question? Ask our team of expert engineers and get a specific answer!
Sign up for the next DPS Factory Training!

Whether you're new to our equipment or you've used it for years, DPS factory training is the best way to get more from your monitoring.
Reserve Your Seat TodayOlder SNMP protocol versions ("legacy SNMP") are those(v1 & v2c) that were released earlier than SNMPv3. These versions don't have the same security level of SNMPv3. They don't include native encryption, and that can bring risks to your company as potential hackers are developing more sophisticated tools every day. In our modern, technology-evolving world, you have to stay on top of security best practices.
Let's walk through how you can efficiently avoid security risks by mediating your legacy SNMP equipment to SNMPv3.
If you're an executive, you need to understand that failing to modernize your SNMP security can threaten your financial performance. Depending on your industry, an embarrassing security incident can lead to competitive disadvantages, create legal liability, or open you up to government fines.
By learning how your team can smoothly evolve past legacy SNMP, you'll see the surprisingly low cost relative to the threats you'll mitigate. Also, learning curves are minimized, and you gain operational efficiency by reducing complexity. This means major ROI.
Now, if you're a manager, you probably made a significant investment in SNMP-capable equipment in the past years. Maybe most of it doesn't support SNMPv3. Think about the growing security risks of unencrypted SNMP and how it could damage this investment. The moment you choose to ignore the threats present by your legacy SNMP gear, a security breakdown becomes only a matter of time.
By converting legacy SNMP to modern SNMPv3 (using one of a few different methods), you can get a clear path to a scalable, future-proof monitoring system that follows security best practices.
And, if you are a system operator, you probably already know that poor planning by your company can cause troubles that you'll need to solve. If a security disaster happens overnight, you'll have to rush to fix this issue. That's why you, better than anyone else, know that some "solutions" can be very difficult to install and maintain.
With the benefit of this quick education on SNMPv3 mediation, you'll be ready when the time comes to act. When you decide to migrate to SNMPv3, you'll minimize wasted effort and learning curves. You'll contribute to boosting your company's efficiency while also making your job easier.
Ultimately, it doesn't matter your position in your company - converting legacy SNMP to SNMPv3 allows you to have a simplified monitoring system. It will be much easier for you to work with and will help you generate better ROI for your company.
Before we dive into specific solutions, it's important to refresh some concepts about SNMP.
Simple Network Management Protocol (SNMP) is a standard internet protocol. This protocol is used in network monitoring applications to collect and organize information from managed devices.
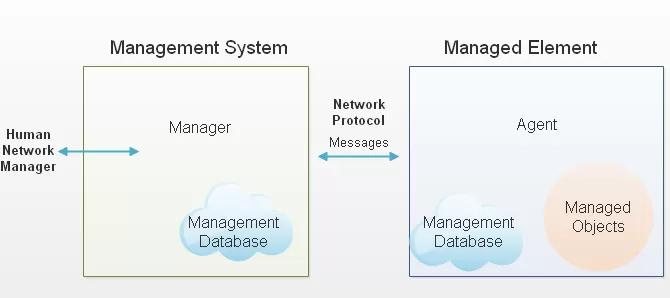
SNMP agents are the devices or programs deployed at each of your remote sites that gather data about other network equipment, organize it, and then send it to the SNMP manager. The SNMP manager will query the agents for information about the equipment and can issue requests to get more information, and in some cases, even set certain properties. The main purpose of an SNMP manager is to join all agents and equipment you monitor into one, easy to monitor, streamlined platform.
Throughout its history, SNMP has undergone several revisions, with each one addressing a major deficit of the previous version. The SNMP protocol has three main versions.
SNMPv1
As the name suggests, this is the first SNMP version. Although it is an open standard and despite its name, this version is not exactly simple. It is not secure either, as it doesn't support encryption or inform command (inform command are used to get an acknowledgment to the master from the agent). Still, it is the only version of SNMP supported by some smaller/older devices.
SNMPv2c
This second version of SNMP brings the inform command feature, improves error handling and improves SET commands (these commands allow the manager to request changes to a managed device). Although SNMPv2c has some improved features, it still doesn't support encrypted messages.
SNMPv3
This newest version of SNMP is the most secure one as it features encryption, but it does require more processor, so firmware updates are not generally possible to upgrade field equipment. Also, not all devices are SNMPv3-compatible. Another thing to keep in mind is that the Inform command is more complicated in v2 than in v2c.
Major networks have to face threats at all times. Lighting, high temperatures, power outages, hackers, are only a few examples of dangers that are always trying to take your network offline. It's impossible to prevent every single network disaster, but there are some threats that are simple to stop before they ever happen.
The SNMP encryption feature, for instance, is an easy way to protect your network against multiple threats. Some of them are:
Terrorism
If you work for a telco, railway, utility, or maybe for a public-safety agency, the risk of terrorism is real. Security is always a problem when it comes to any network. And with network devices, remote access makes it even easier for someone to get into your system - without ever having to physically go to your facilities. SNMP encryption defends your network against hacking by scrambling messages as they are sent.
Outages
People with malicious intentions don't just stop once they have hacked your network. They want to create chaos. For that, they need to have access to your equipment and information. Once inside your network, they are able to toggle relays, change passwords, login info, and even disable entire systems.
Usually these issues lead to outages - that could be prevented with SNMP encryption.
Government Fines
The government regulates most industries to tell them what security layers need to be deployed. If your network is not in compliance with these regulations, you might be fined. Some industries are also subject to government fines for outages. They can be very expensive - thousands of dollars for each minute of network downtime, for example.
Legal Liability
Besides government fines, there's also the possibility of being legally responsible if someone is able to hack your system and gain access to customer and other sensitive information. You don't need to look very deeply through major recent headlines to see how big a deal these consumer-information compromises can be.
Network Operator Confusion
Any time you have multiple systems and multiple standards operating in your network, you have to increase training requirements for new staff. The chance that someone makes a mistake is increased, and you need to spend more time training. Merging all your SNMP to modern standards eliminates this risk.
Through SNMPv3 encryption, you will be protecting your network against hacking, outages, unhappy customers, and government fines. It's a simple and easy solution that will save both time and money down the line.
If your network has evolved over time (as most networks have), you have a problem. Many of your older SNMP-enabled devices don't support secure, encrypted SNMPv3.
Since encryption is an intensive operation for small hardware, firmware updates will not save you. Also, you most probably can't replace all of your SNMP-based equipment all at once. It's very rare for companies to have the budget to simultaneously upgrade all the equipment that was installed over many years.
To solve this issue, you need an SNMPv3 mediation plan that will allow you to convert SNMPv1 and v2c to the most secure v3.
There are two main ways to make SNMP mediation plans happen. The first involves a centralized master station. The second involves multiple smaller devices (this option is also known as the decentralized option).
In this option, a central master station is used to convert SNMP messages (traps) to SNMPv3. All older SNIP-enabled devices will report to this mid-level master. Traps will be converted and forwarded as v3 traps. So you only have to buy one device, as well as install and configure this single device. Unless you have a very small network, this is going to be the simplest, cheapest way for you to upgrade to SNMPv3.
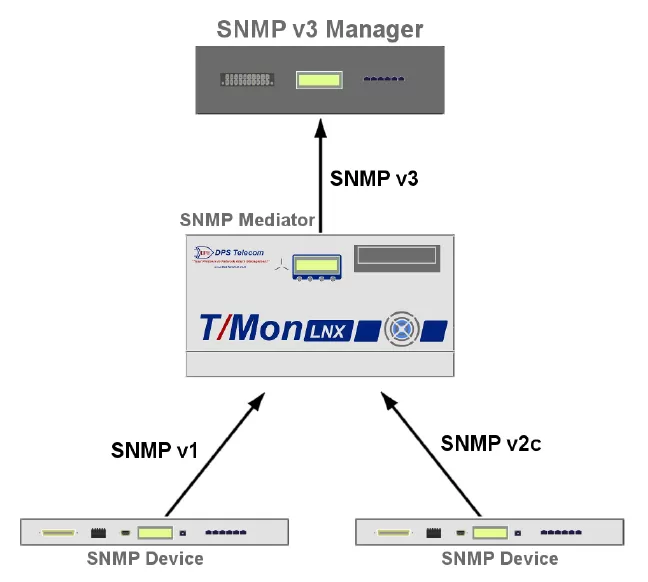
However, there are some limitations to using a single master station:
You have a single point of failure
You can choose to install a redundant pair of masters to solve this issue.
You'll still be using unencrypted SNMP until traps reach the central master
Your overall network architecture should be the main factor in your decision. Do you have other security in place to compensate for the SNMPv1/v2c segments?
Here, individual remote telemetry devices (RTUs) are used to convert SNMP to encrypted v3 at each of your individual sites. This decentralizes your points of failure and allows for conversion before SNMP leaves each building.
The alternative to a central master is a decentralized fleet of SNMPv3 converters. These devices are small (usually 1 RU) and they can handle a reasonable number of inbound SNMP trap messages. Since you'll be deploying multiple converters, each one has to handle just part of the total SNMP traffic.
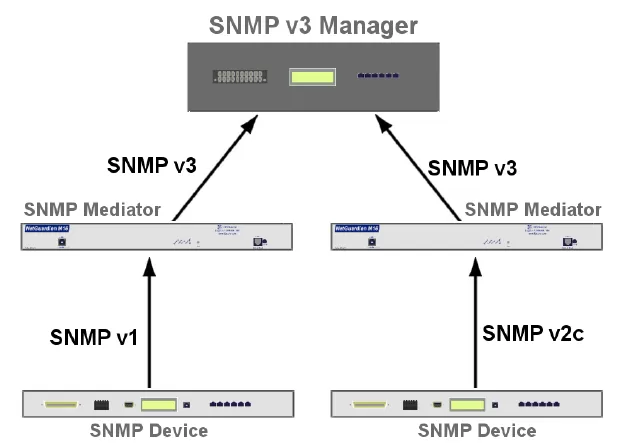
Although this is not the cheapest option (in most of the cases), this decentralized alternative deals with many potential problems of a single master station:
You'll eliminate the single point of failure
The loss of a single converter device will have no big effect on any other device.
No unencrypted SNMP leaves the site
With a device in each remote site, you won't have unencrypted SNMP traffic traveling across any significant area of your network.
Remote converters can handle other functions
You can generally take care of other monitoring/control tasks using included functions on the converter device.
If you can handle the possible one-time increase in purchasing and select the option B, you'll gain many advantages over option B. Always remember that any alternative you decide to choose is still better than simply doing nothing.
Whether you want to mediate your legacy SNMP to v3, or you've just added a site and you need a new SNMPv3 RTU, you need to know how to choose the best equipment.
Choosing an SNMPv3 alarm remote (RTU) to buy is an important decision and should be considered carefully. The following steps will help you be sure you're getting the best SNMPv3 RTU for your network monitoring needs.
You might need to mediate SNMPv1 and v2c, or you might just want an SNMPv3 RTU. But, what other things are you looking for?
Before choosing a solution, ask yourself the following questions:
What are my capacity needs?
What devices do I need to monitor?
How many units do I need?
What is my budget?
What type of network growth my device should be able to accommodate?
When taking into consideration your options, ask yourself:
Does this RTU fit my site (small, medium, or large)?
Does this RTU allow for future expansions?
One important thing to do is to think beyond the scope of just SNMP, you should see what other features your potential device offers in order to get the most bang for your buck.
Also, don't compromise on the things you really need or spend budget on capabilities that you'll never use. Your device should fit all your specs.
Price is - of course - important, but you also should compare what each company is willing to give you for that price. Usually, the cheapest option isn't actually the best. When it comes to remote monitoring, you definitely get what you pay for.
Make sure that each company you're considering has quoted you something that really fits your network requirements. Having to compromise on a feature you need or having to pay for something you won't ever use simply means that this company is not your best fit.
When you're studying your quote, there are some things to keep in mind:
Does the company offer tech support? If so, how much do you have to pay for it?
Does the company offer training?
Can the company provide you with testimonials and referrals that you can contact?
How long have they been working with remote monitoring equipment?
Once you've looked over all the information you have, the choice is usually pretty obvious. You can now make an informed decision.
Despite the advantages of an open standard, early versions of SNMP (v1 and v2c) were not built with security in mind. This is a big challenge for security-conscious organizations. Many companies are now migrating to SNMPv3 due to its encryption feature.
In order to be able to mediate your legacy SNMP versions to SNMPv3, you can deploy a central SNMP manager that is able to translate older v1 and v2c to v3. Or you can deploy a fleet of RTUs at your remote sites to convert traps into SNMPv3.
Both options can be the best alternative for you. It only depends on your unique network. However, no matter which option you choose, to have an efficient SNMPv3 mediation process in place, you need to find the right-fit device for your scenario.
As a vertical integrated remote monitoring equipment provider, we control every step of our manufacturing process. We are able to create perfect-fit solutions for our clients because - from sales to engineering to production to tech support - we handle all our operations in-house.
We customize our devices to meet your exact needs, so our solutions are the right fit and you won't have to buy a lot of extraneous hardware and software. See how our customized solutions can enhance your network security and performance, while also saving your money, call us today.

Morgana Siggins
Morgana Siggins is a marketing writer, content creator, and documentation specialist at DPS Telecom. She has created over 200 blog articles and videos sharing her years of experience in the remote monitoring industry.