Check out our White Paper Series!
A complete library of helpful advice and survival guides for every aspect of system monitoring and control.
1-800-693-0351
Have a specific question? Ask our team of expert engineers and get a specific answer!
Sign up for the next DPS Factory Training!

Whether you're new to our equipment or you've used it for years, DPS factory training is the best way to get more from your monitoring.
Reserve Your Seat TodayManaging and modifying who can log into your critical network gear - across hundreds of routers, RTUs, and switches - is a big challenge. Ideally, you can achieve the opposite: being able to revoke a tech's access instantly, without visiting a single site.
That's what you get with centralized RADIUS authentication. And frankly, it's what your infrastructure demands if you're serious about uptime, security, and operational control.
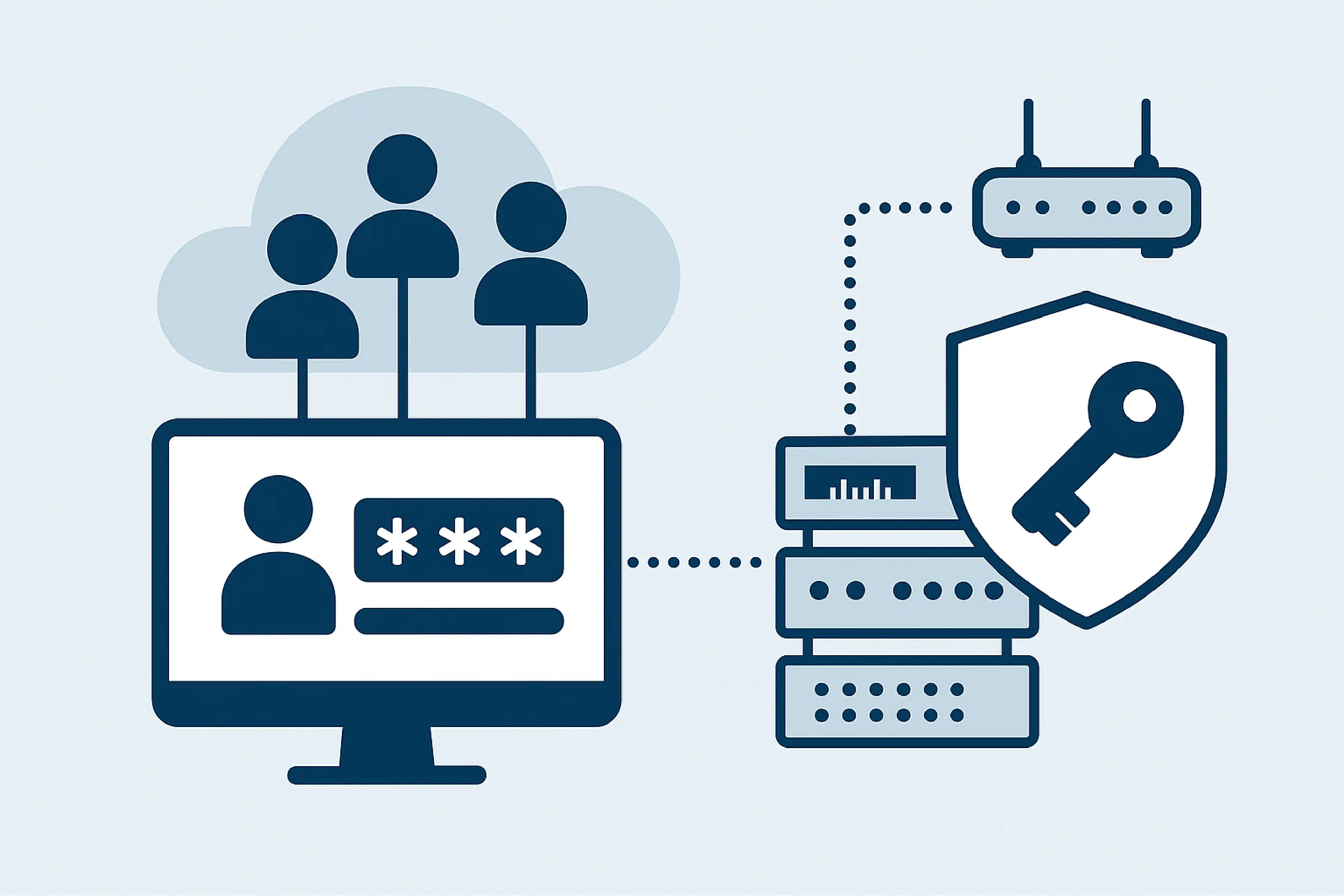
Most network engineers we talk to know that local logins are a problem. However, they often underestimate just how much risk this creates.
When you're managing a large network - with dozens or hundreds of remote sites - keeping access secure gets exponentially harder when every device maintains its own list of usernames and passwords.
Some issues that can (and often do) arise include:
Even worse, if you're in a regulated industry - like power utilities under NERC CIP or telcos handling sensitive public infrastructure - this kind of access control failure can get you fined or cause a major security incident.
The bottom line is local login management doesn't scale. It's time-consuming, error-prone, and fundamentally insecure.
Most companies try to patch their access control systems over time. Maybe you've done one (or all) of the following:
These all seem like improvements on paper. But they're still not a single centralized intelligence. That would mean the ability to manage access, log activity, and respond to threats across your entire network from a single interface.
If your access control solution can't do that, it's not solving the root problem - it's just delaying it.
What if, instead of worrying about forgotten logins or rogue access, you could:
That's not a wishlist. It's what centralized RADIUS authentication (done right) can do.
That's precisely why we've added RADIUS support to our NetGuardian RTUs. We want you to have the ability to add them to your overall access management system.
RADIUS (Remote Authentication Dial-In User Service) isn't new. However, modern, smart RADIUS systems go far beyond basic yes/no authentication.
Real access control systems should offer:
Know what's happening right now. See login events in real time, including who accessed what device, from where, and whether they succeeded or failed.
Don't give field techs the keys to the entire kingdom. With role-based policies, you can restrict access to only what's necessary - by role, geography, or equipment type.
Instant alerts for failed logins, lockouts, or suspicious login patterns help you stop security threats before they escalate.
Only engineers need CLI access to core routers. Contractors don't need access beyond one site. RADIUS lets you enforce these boundaries automatically.
Skip the terminal windows. A secure, centralized web GUI makes it easy to manage users, assign roles, and audit activity - whether you're in the NOC or on the road.
Sync user accounts with your existing directory structure. This gives you:
Fine-grained control of who can log in where:
Two-factor authentication is increasingly mandated - especially for sensitive gear.
Use:
MFA drastically reduces the effectiveness of stolen credentials, since the second authentication method is still required...
A powerful web interface means easier administration, lower training requirements, and fewer costly errors.
RADIUS should support secure authentication protocols to protect login data in transit.
Security logs should be available live and exportable to your master alarm systems (like T/Mon).
Your RADIUS system must work with:
Here's the good news: If you already use NetGuardian RTUs from DPS, you're almost there.
Every current-generation NetGuardian includes:
There's no need for additional hardware. Your access control system is already in place - you just need to activate and configure it.
The NetGuardians with RADIUS support other open standards, giving you additional compatibility with devices like:
Without centralized control, updating user access means logging into dozens of devices, applying changes manually, and hoping you didn't miss one.
With smart RADIUS:
RADIUS helps you sleep better knowing there aren't leftover credentials lurking in forgotten devices.
Here's what's happening in the real world:
If your current solution doesn't give you visibility, control, and rapid response, it's time for an upgrade.
Anyone can slap a RADIUS label on a product spec sheet.
At DPS, we've spent the last 30+ years building monitoring systems that secure real infrastructure. We're not an access control company trying to sell into telecom. We're telecom infrastructure people who saw a problem and solved it.
Our NetGuardian RTUs and T/Mon master stations are designed for:
And our RADIUS implementation reflects that experience.
You probably don't have time to research every option out there. You've got sites to maintain and SLAs to hit.
So let me make this easy. Give me a call, and I'll help you:
Whether you're starting from scratch or optimizing an existing system, I'll guide you through it.
Call me at 559-454-1600
Or email: sales@dpstele.com
We'll give you real answers and practical advice.

Andrew Erickson
Andrew Erickson is an Application Engineer at DPS Telecom, a manufacturer of semi-custom remote alarm monitoring systems based in Fresno, California. Andrew brings more than 19 years of experience building site monitoring solutions, developing intuitive user interfaces and documentation, and opt...