Check out our White Paper Series!
A complete library of helpful advice and survival guides for every aspect of system monitoring and control.
1-800-693-0351
Have a specific question? Ask our team of expert engineers and get a specific answer!
Sign up for the next DPS Factory Training!

Whether you're new to our equipment or you've used it for years, DPS factory training is the best way to get more from your monitoring.
Reserve Your Seat TodayTransit infrastructure is evolving faster and faster.
From smart traffic signals to connected train stations and vehicle telemetry systems, today's transit networks rely heavily on data and connectivity. But as the tech stack grows, so does the threat landscape. What used to be a self-contained signal cabinet is now a potential cyberattack target.
As public transit agencies deploy more digital systems to improve efficiency, safety, and rider experience, they must also face a hard truth: Connectivity without cybersecurity is a disaster waiting to happen.
Using the advice from Metro's transit cybersecurity blog, let's explore:
Whether it's managing buses, trains, or an entire intermodal transportation network, let's dive into strengthening your security strategy.

Transit systems are known for being visible, essential, and increasingly dependent on connected systems. As a result, these systems have become prime targets for cyberattacks.
Train control systems, automated fare collection, surveillance cameras, passenger Wi-Fi, digital signage, and even HVAC in stations are now managed via networked infrastructure. That creates dozens (if not hundreds) of possible access points for malicious actors.
And the more connected your network becomes, the more one weak link can compromise the whole chain.
While some may laugh off "Hollywood-style" scenarios like all-green lights (causing traffic accidents and jams), the technical possibility of real-world network manipulation is no joke. Every unsecured port, protocol, or connection is a vulnerability just waiting to be exploited.
In fact, we've already seen ransomware attacks shut down transportation networks, including railways, port terminals, and urban transit agencies. These weren't hypothetical cases - they were extremely expensive, real-world lessons in the cost of underprepared infrastructure.
Transit agencies are trying to do the right thing. Many have deployed firewalls, VPNs, and even multi-factor authentication.
But here's the problem: many of these defenses are designed for office IT - not industrial transit systems.
Transit infrastructure has unique challenges:
In some cases, you might not even know how many network-connected assets you have, let alone how secure they are. With multiple vendors, mismatched firmware versions, and inconsistent update practices, visibility can be half the battle.
Plus, with tight budgets and limited staff resources, you've got a recipe for under-protected, overexposed infrastructure.
What would true cybersecurity look like for your transit systems?
It's more than just "installing antivirus." It's about architecture, visibility, and layered defenses - designed with transit in mind.
When these fundamentals are in place, your network becomes far harder to compromise - and far easier to recover if something does go wrong.
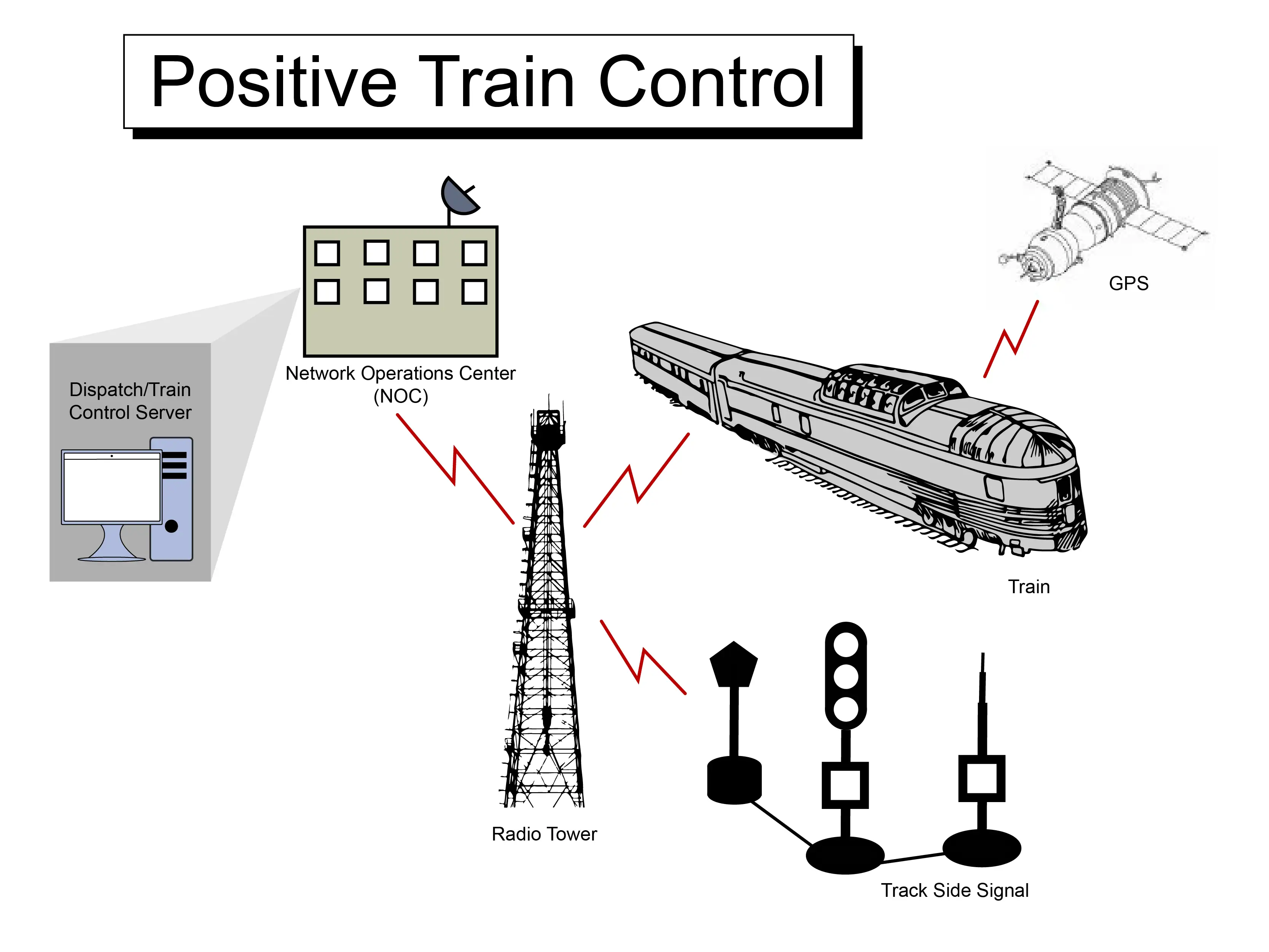
At DPS, we've helped transit agencies, utilities, and other infrastructure operators secure their networks for over 30 years. Our specialty is building rugged, secure, and intelligent remote monitoring and control solutions.
If you're dealing with the cybersecurity challenges of transit infrastructure, here's how DPS gear can help you take control - without replacing all your legacy hardware or locking into one vendor's ecosystem.
Our NetGuardian series of Remote Telemetry Units (RTUs) are built to bring intelligence, control, and monitoring to the edge of your network. Whether it's a signal cabinet, a remote substation, a train platform, or a communications node, a NetGuardian can:
NetGuardians are built in the USA, backed by lifetime support, and field-tested by Class I railroads, DOTs, water utilities, and telecom giants. We design these units for hostile environments and critical uptime.
Transit agencies often struggle to secure older equipment that was installed before the era of modern networking. DPS provides SNMP mediation and protocol conversion, allowing you to:
With DPS mediation, you can secure older systems without a full forklift upgrade. That's budget-smart and operationally safer.
As transportation systems grow more connected and cities adopt "smart infrastructure," standards like NTCIP are becoming even more important.
The National Transportation Communications for Intelligent Transportation System Protocol (NTCIP) ensures interoperability across devices from different vendors - but it must also evolve to ensure secure communication.
That means:
At DPS, we support these efforts by building devices that are:
We work with you to make sure that your implementation is both standards-compliant and secure - two things that don't always go hand in hand.
Unlike "bolt-on" security from big equipment vendors, DPS devices are purpose-built for network visibility, security, and control.
We don't make buses. We don't make trains. We make the gear that protects those systems from going down - or getting hacked.
When you deploy DPS gear, you get:
Our systems are built for mission-critical use and supported by engineers who actually understand transit operations. Whether you're trying to avoid NTCIP vulnerabilities, mediate SNMP across hundreds of sites, or secure a signal system that was installed in the '90s, we've got you covered.
Transit systems don't get second chances.
When infrastructure fails - whether due to a cyberattack, power outage, or human error - the impact is immediate. Riders are stranded, schedules unravel, and trust erodes.
You need gear that's built with purpose, proven in the field, and backed by a team that lives and breathes secure infrastructure.
At DPS Telecom, we help transit leaders like you:
Call us now at 559‑454‑1600
Email us at sales@dpstele.com
The future of public transportation depends on secure, reliable systems. Let's make sure yours is ready.

Andrew Erickson
Andrew Erickson is an Application Engineer at DPS Telecom, a manufacturer of semi-custom remote alarm monitoring systems based in Fresno, California. Andrew brings more than 19 years of experience building site monitoring solutions, developing intuitive user interfaces and documentation, and opt...