Check out our White Paper Series!
A complete library of helpful advice and survival guides for every aspect of system monitoring and control.
1-800-693-0351
Have a specific question? Ask our team of expert engineers and get a specific answer!
Sign up for the next DPS Factory Training!

Whether you're new to our equipment or you've used it for years, DPS factory training is the best way to get more from your monitoring.
Reserve Your Seat Today
|
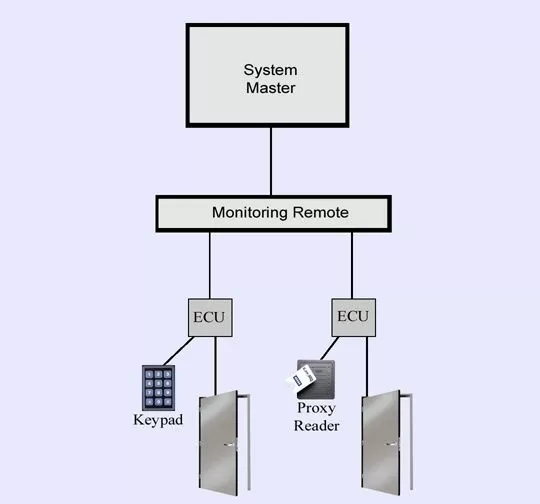
Individual user profiles can even be assigned to temporary workers or outside contractors, giving them the access for only the few days they will need it. This guarantees you will know who is coming and going at all times, allowing you to monitor work performance, even of your outside help.
The system master can also provide detailed reports on access events using this database. All access event information is stored directly within the master database, allowing you to create a history log all of all access events during any given period. This can be particularly useful in the event of theft or vandalism at one of your sites. This data can be combined with network alarm data as well, letting you know immediately if a visitor to your site has tampered with your mission-critical equipment.
Our integrated building access systems are backed by a 30-day, no-risk guarantee. Test the proposed solution under real-world conditions for 30 days, and if, at any time during that period, you decide for any reason that our solution will not meet your access control needs, you can cancel your order with no further obligation. It sounds crazy, but in the 15 years we've offered our no-risk guarantee, not one client has returned a custom solution.
|