A high-quality building access system will enhance the security of your sites.
This guide to will show you how to ensure the safety of your revenue-generating equipment.
1-800-693-0351
Have a specific question? Ask our team of expert engineers and get a specific answer!
Sign up for the next DPS Factory Training!

Whether you're new to our equipment or you've used it for years, DPS factory training is the best way to get more from your monitoring.
Reserve Your Seat TodayHave you ever had to deal with an intruder? What about that key ring that got misplaced when your employee took them home by accident? If you can relate, then you know how difficult security issues can be to deal with. A lost key can pose a huge risk if it falls into the wrong hands, and replacing all the locks it could have operated can get rather pricey, not to mention if that key happened to be a key ring with a key to every lock in the building. Even if it didn't get lost, how many times have you had a copy made of a key that said "DO NOT DUPLICATE"? When security issues arise, it's far better to be prepared than to have to recover any losses. This is where building access systems have shown that they are worth more than their weight in gold.
Having a well-designed access control system in place can be far more effective than placing a security guard at every door. Security guards are still people, and people can make mistakes. How many people do you know that can memorize well over 1,000 individuals, which places they can access, which times of day, what days, and how often? I personally haven't met any that have a memory that strong.
A Building Access System (BAS) is a comprehensive building management system that integrates into an existing alarm management platform. With the system in place, a log of all site access, including the time of day and location that access was granted, is maintained. Additional features include the ability to report intrusions, excessive access attempts, a centralized entry management station, and the abilities to further limit access points beyond that of a key and an alarm.
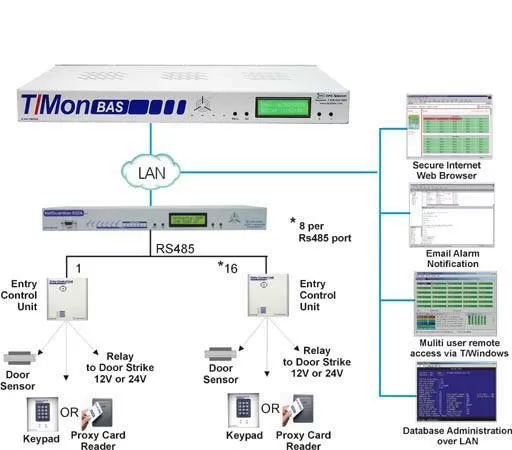
With the incorporation of keypads and proximity card sensors, individuals can be granted or denied access based on permissions stored into a secure database. These privileges can be limited, edited, or removed for any reason from within the system. This is especially useful if your company works with contractors or temporary employees since their access can be removed outside of the times they are supposed to be on-site.
With the incorporation of motion-sensors, electromagnetic door locks, and timers, many other accessibility features can be maintained as well. If a sensor detects an individual walking towards a door, a signal can be sent allowing the door to unlock before they even grab the handle. Imagine being able to walk down a hallway, have the lights turn on before you need them, the door unlock for you, and then once the door shuts, everything returns to its previous state.
These are only a few of the tasks that a proper Building Access System can perform. For further ideas and possibilities, contact a proven security solutions expert today.