Download our free SNMP White Paper. Featuring SNMP Expert Marshall DenHartog.
This guidebook has been created to give you the information you need to successfully implement SNMP-based alarm monitoring in your network.
1-800-693-0351
Have a specific question? Ask our team of expert engineers and get a specific answer!
Sign up for the next DPS Factory Training!

Whether you're new to our equipment or you've used it for years, DPS factory training is the best way to get more from your monitoring.
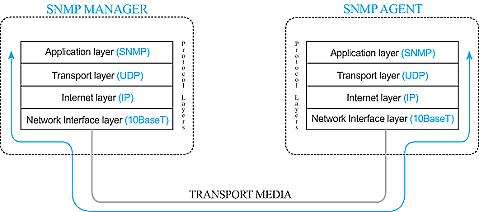
Reserve Your Seat TodayNow, we continue to examine the Simple Network Management Protocol (SNMP). We'll focus specifically on the layered communication model used to exchange information. Our last article focused on the structure of SNMP messages, however an SNMP message is not sent by itself. It is wrapped in the User Datagram Protocol (UDP), which in turn is wrapped in the Internet Protocol (IP). These are commonly referred to as layers and are based on a four-layer model developed by the Department of Defense (you may recall the DoD origins of the Internet).
SNMP resides in what is called the Application layer. UDP resides in the Transport layer. IP resides in the Internet layer (somewhat obvious). The fourth layer is the Network Interface layer where the assembled packet is actually interfaced to some kind of transport media (i.e., twisted pair copper, RG58 co-axial or fiber).
While this multi-layer model may seem a bit confusing, it effectively isolates the tasks of communication. In the end, it assists in designing and implementing a network.
To illustrate the function of this layered model, let's look at a single SNMP GET request from the agent's perspective. The SNMP manager wants to know what the Agent's System Name is and prepares a GET message for the appropriate OID. It then passes the message to the UDP layer. The UDP layer adds a data block that identifies the manager port. This is where the response packet should be sent. It's also the port on which it expects the SNMP agent to be listening for messages. The packet thus formed is then passed to the IP layer. Here a data block containing the IP and Media Access addresses of the manager and the agent is added. Then, the entire assembled packet gets passed to the Network Interface layer. The Network Interface layer verifies media access and availability and places the packet on the media for transport.
The packet works its way across bridges and through routers (the modern equivalent of over the river and through the woods) based on the IP information. Then it finally arrives at the agent. Here it passes through the same four layers in exactly the opposite order as it did at the manager. First, it is pulled off the media by the Network Interface layer. After confirming that the packet is intact and valid, the Network Interface layer simply passes it to the IP layer. The IP layer verifies the Media Access and IP address and passes it on to the UDP layer where the target port is checked for connected applications. If an application is listening at the target port, the packet is passed to the Application layer. If the listening application is the SNMP agent, the GET request is processed as we have discussed in previous articles. The agent response then follows the identical path in reverse to reach the manager.
Understanding this layered model makes it easier to troubleshoot communication problems. These might include TCP/IP problems, MIB problems, or a variety of other types. When there is a problem, you can simply trace it down, out one end, into, and up the other. LAN/WAN link and activity status indicators provide some visibility to the Network Interface layer. ICMP echo requests and responses (Pings) provide some information regarding the proper functioning of the IP layer. SNMP processing indicators can be used to verify the passage of the packet through the UDP layer. They also check the functioning of the Application layer. Each step can be verified independently until all steps are working correctly for end-to-end communication.
SNMP is a standard protocol that has wide acceptance in the industry and is flexible enough to describe almost anything. Because of these advantages, many network managers have come to believe that SNMP should be used for all network monitoring applications.
SNMP certainly has its place in an effective telecom network management solution. This doesn't mean that any off-the-shelf SNMP manager can provide adequate visibility and control of your network, though.
The typical off-the-shelf SNMP manager is not designed for displaying and processing telemetry data for effective network monitoring. This counts double for the kind of real-world monitoring tasks network managers most need performed. These capabilities can be added to an SNMP manager, but it usually requires substantial custom software development.
Before you buy... make sure you avoid these 7 common mistakes.Relying on off-the-shelf SNMP systems for mission-critical telemetry is a major mistake. What if you're switching from traditional telemetry or integrating non-SNMP monitoring with an SNMP-based system? An off-the-shelf SNMP manager will not provide what you need and expect. You won't get detailed alarm data. Before you commit to an SNMP monitoring solution, you need to make sure it supports key network alarm monitoring functions.
There are seven common mistakes network managers typically make when integrating SNMP and non-SNMP monitoring. Your SNMP implementation will be successfully only if you can avoid them...